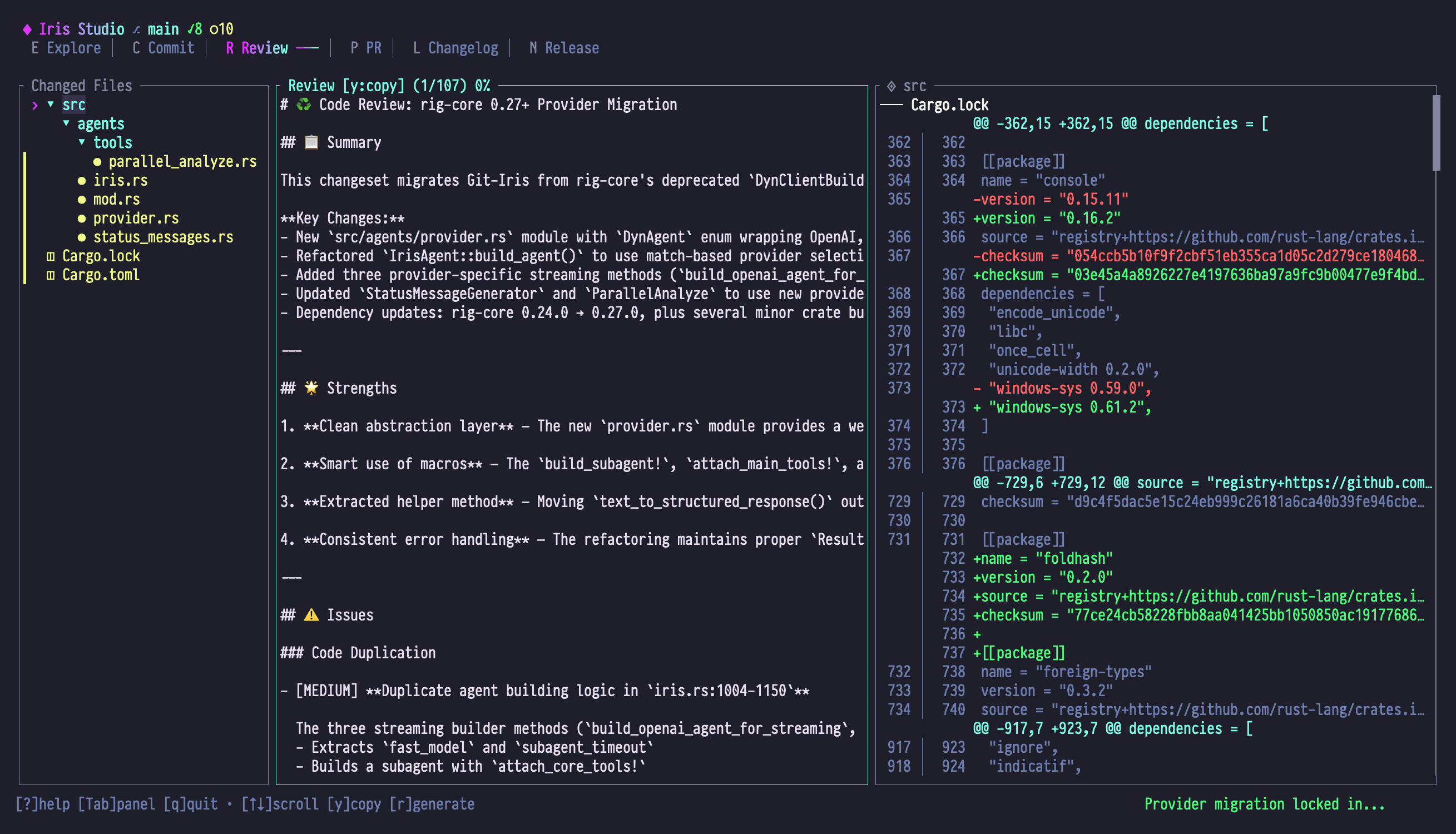
Review Mode
Review Mode provides AI-powered code reviews analyzing security, performance, best practices, and potential bugs. Get comprehensive feedback before committing or creating PRs.
When to Use Review Mode
- Pre-commit quality checks: Review changes before committing
- PR preparation: Catch issues before reviewers see them
- Learning best practices: Understand why certain patterns are recommended
- Security audit: Identify potential vulnerabilities
- Performance analysis: Find bottlenecks and inefficiencies
Panel Layout
| Panel | Content |
|---|---|
| Left | Changed files in selected range with directory tree and ref selection |
| Center | Markdown-formatted review with categorized findings and severity indicators |
| Right | Unified diff view with syntax highlighting and hunk navigation |
Left Panel: Changed Files
- Files with changes in selected range
- Directory tree structure
- Git status indicators
- Ref selection (from/to)
Center Panel: Review Output
- Markdown-formatted review
- Categorized by dimension (Security, Performance, etc.)
- Severity indicators (✓, ⚠️, ✗)
- Line number references
- Scrollable multi-section output
Right Panel: Diff View
- Unified diff for context
- Syntax-highlighted changes
- Hunk navigation
- Multi-file diff
Essential Keybindings
File List (Left Panel)
| Key | Action |
|---|---|
| j / ↓ | Select next file |
| k / ↑ | Select previous file |
| h / ← | Collapse directory |
| l / → | Expand directory |
| Enter | Load file diff (focus right panel) |
| f | Select "from" ref (base) |
| t | Select "to" ref (target) |
| r | Generate review |
| g / Home | Jump to first file |
| G / End | Jump to last file |
Review Output (Center Panel)
| Key | Action |
|---|---|
| j / ↓ | Scroll down |
| k / ↑ | Scroll up |
| Ctrl+d / PgDn | Page down |
| Ctrl+u / PgUp | Page up |
| g / Home | Jump to top |
| G / End | Jump to bottom |
| r | Regenerate review |
| Shift+R | Reset (clear review) |
| y | Copy review to clipboard |
Diff View (Right Panel)
| Key | Action |
|---|---|
| j / ↓ | Scroll down |
| k / ↑ | Scroll up |
| [ | Jump to previous hunk |
| ] | Jump to next hunk |
| n | Jump to next file |
| p | Jump to previous file |
| Ctrl+d / PgDn | Page down |
| Ctrl+u / PgUp | Page up |
Ref Selection
Press f or t to select from/to refs. The modal displays a filterable list of branches and tags with type-to-search functionality.
Default Refs
- From:
main(ormaster) - To:
HEAD(current state)
Common Ranges
| From | To | Reviews |
|---|---|---|
main | HEAD | All changes on current branch |
v1.0.0 | v1.1.0 | Changes between releases |
abc123f | HEAD | Changes since specific commit |
origin/main | HEAD | Local changes not pushed |
Review Dimensions
Iris analyzes code across multiple dimensions:
🔒 Security
- SQL injection risks
- XSS vulnerabilities
- Authentication/authorization issues
- Cryptographic weaknesses
- Input validation gaps
- Secret exposure
⚡ Performance
- Algorithmic complexity (O(n²) loops, etc.)
- Memory leaks
- Inefficient queries
- Unnecessary allocations
- Hot path optimizations
- Caching opportunities
✨ Best Practices
- Code organization
- Naming conventions
- Error handling patterns
- Testing coverage
- Documentation quality
- SOLID principles
🐛 Potential Bugs
- Null/undefined dereferencing
- Off-by-one errors
- Race conditions
- Resource leaks
- Type mismatches
- Edge case handling
🧹 Code Quality
- Duplication (DRY violations)
- Complexity (cyclomatic, cognitive)
- Readability
- Maintainability
- Testability
📚 Documentation
- Missing docstrings
- Outdated comments
- Unclear naming
- API documentation
- README accuracy
Review Output Format
# Code Review
## Summary
Reviewed 3 files with 145 additions and 32 deletions.
Overall: ✓ Good with minor improvements suggested.
## Security
✓ No critical security issues found.
⚠️ Consider validating user input in `src/handlers/commit.rs:45`
Current implementation trusts all input from message editor.
Suggestion: Add length limits and sanitize special characters.
## Performance
✓ Efficient use of iterators throughout.
✗ Potential O(n²) issue in `src/studio/state.rs:123`
Nested loop scans all files for each commit.
Suggestion: Index files by commit ID for O(1) lookups.
## Best Practices
✓ Follows Rust idioms well.
✓ Good error handling with Result types.
⚠️ Consider extracting `sync_file_selection()` to a trait
This pattern is repeated in 3 different handlers.
Suggestion: Create a `FileSync` trait for reuse.
## Potential Bugs
✓ No obvious bugs detected.
## Code Quality
Overall quality: High
⚠️ Function `handle_commit_key` is complex (cyclomatic: 12)
Consider splitting into smaller functions.
## Documentation
⚠️ Missing docstring for `EmojiMode::Custom`
Add documentation explaining when to use this variant.
## Recommendations
1. Add input validation to message editor
2. Optimize file lookup in state management
3. Extract file sync logic to shared trait
4. Document EmojiMode variants
Estimated time to address: 2-3 hoursSeverity Indicators
- ✓ (Green): Good, no issues
- ⚠️ (Yellow): Warning, minor improvement
- ✗ (Red): Error, significant issue
Workflow Examples
Example 1: Pre-Commit Review
Goal: Check changes before committing
- Make code changes
- Switch to Review mode (Shift+R)
- Default refs are
main..HEAD(perfect for feature branch) - Press r to generate review
- Read through each dimension
- Press / to chat: "Explain the O(n²) issue you found"
- Fix issues in your editor
- Press r to review again
- When ✓ across all dimensions, switch to Commit mode (Shift+C)
Example 2: PR Preparation
Goal: Get feedback before creating pull request
- Finish feature branch
- Switch to Review mode
- Press f to select from ref:
origin/main - Press t to select to ref:
HEAD - Press r to generate review
- Address all ✗ and ⚠️ items
- Press y to copy review to clipboard
- Paste into PR description as "Self-Review" section
Example 3: Release Audit
Goal: Review all changes between versions
- Open Review mode
- Press f → select
v1.0.0 - Press t → select
v1.1.0 - Press r to generate review
- Focus on Security dimension (scroll to section)
- Document any breaking changes found
- Copy review with y
- Use as release audit documentation
Example 4: Learning from Reviews
Goal: Understand best practices by asking Iris
- Generate review (r)
- See warning: "Consider using iterators instead of for loops"
- Press / to open chat
- Ask: "Show me how to rewrite that loop with iterators"
- Iris provides example code
- Press Shift+E to switch to Explore mode
- Navigate to the file
- Press w on the loop to understand its history
- Refactor based on learning
Example 5: Security-Focused Review
Goal: Audit for security issues only
- Generate review
- Scroll to Security section with j/k
- For each ⚠️ or ✗:
- Note the line number
- Press Tab to focus diff panel
- Navigate to that line with j/k
- Press / to ask: "How would you exploit this?"
- Fix vulnerabilities
- Press r to verify fixes
Special Features
Context-Aware Analysis
Iris reads project documentation to understand:
- Architecture patterns: From CLAUDE.md
- Coding standards: From README or CONTRIBUTING.md
- Agent behavior: From AGENTS.md
Reviews are customized to your project's standards.
Diff-Integrated Review
Line number references in review correspond to diff view:
Review says: Diff shows:
⚠️ Line 45 @@ -40,6 +40,10 @@
42 pub fn new() {
43 Self {
44 mode: Auto,
45 editing: false, ← Line 45Press Tab to jump between review and diff.
Chat Integration
Ask follow-up questions about review findings:
You: Why is the O(n²) loop a problem here?
Iris: The nested loop in state.rs processes each commit
against all files. For 100 commits × 500 files, that's
50,000 iterations.
With indexed lookup:
1. Build HashMap<CommitId, Vec<FileId>> // O(n)
2. Look up files for each commit // O(1)
Total: O(n) instead of O(n²)
You: Show me the indexed version
Iris: [Provides code example]Incremental Review
After fixing issues:
- Press r to regenerate
- Iris focuses on new issues only (remembers context)
- Confirms fixes: "✓ O(n²) loop now uses indexed lookup"
Review Modes
Quick Review (Default)
Fast analysis focusing on critical issues:
- Security vulnerabilities
- Obvious bugs
- Major performance problems
Takes 10-30 seconds.
Deep Review (Future)
Comprehensive analysis including:
- Test coverage gaps
- Documentation completeness
- Architecture adherence
- Dependency analysis
Takes 1-3 minutes.
Tips & Tricks
1. Review Before Committing
Make it a habit:
- Write code
- Shift+R → Review
- Fix issues
- Shift+C → Commit
2. Use Chat for Explanations
Don't guess what warnings mean:
- See ⚠️ → Press / → Ask "Explain this warning"
- Iris provides detailed context and examples
3. Compare with Upstream
Before merging to main:
- From:
origin/main - To:
HEAD - Reviews what will land in production
4. Save Reviews for PRs
Copy review (y) and paste into:
- PR description
- Commit message (for complex changes)
- Team wiki (as examples)
5. Focus on One Dimension
Use j/k to scroll directly to:
- Security (if handling user input)
- Performance (if optimizing hot paths)
- Best Practices (for mentorship/learning)
6. Iterative Improvement
Don't try to fix everything at once:
- First pass: Fix ✗ (errors)
- Second pass: Address ⚠️ (warnings)
- Third pass: Polish ✓ sections
Troubleshooting
Review is empty
Symptom: Center panel shows "No review generated"
Fix:
- Check that from/to refs are different
- Ensure there are actual changes in range
- Press r to manually trigger
- Check status bar for errors
Review takes too long
Symptom: Iris status shows "Thinking..." for >1 minute
Cause: Very large diff (1000+ lines)
Fix:
- Narrow the ref range (fewer commits)
- Review files individually (select in left panel)
- Use chat instead: "Review the security of iris.rs"
Line numbers don't match
Symptom: Review mentions line 45, but diff shows line 50
Cause: Line numbers are from after changes (in "to" ref)
Fix: Navigate diff to find context around that area.
No security issues found but I'm suspicious
Symptom: Review says "✓ No security issues" but you're not convinced
Fix:
- Press / to open chat
- Ask specific questions: "Could this be vulnerable to XSS?"
- Request focused analysis: "Review line 45 for SQL injection"
Next Steps
- Use review findings to improve Commit Messages
- Combine with Explore Mode to understand flagged code
- Generate PR Descriptions that include review summary
- Learn Chat for detailed review discussions
